Spring Security认证授权机制全面解析
Spring Security 认证与授权机制深度解析
一、认证机制详解
1.1 认证流程核心组件
Spring Security 的认证流程围绕几个核心组件构建:
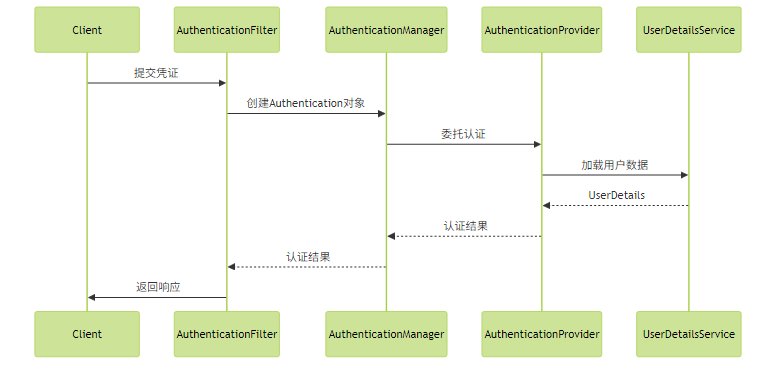
关键组件说明:
AuthenticationManager: 认证入口接口ProviderManager: 默认实现,委托给多个AuthenticationProviderAuthenticationProvider: 具体认证逻辑实现UserDetailsService: 加载用户核心数据
1.2 常见认证方式实现
表单登录配置示例
@Configuration
@EnableWebSecurity
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.formLogin()
.loginPage("/custom-login") // 自定义登录页
.loginProcessingUrl("/auth") // 认证处理URL
.defaultSuccessUrl("/home", true)
.failureUrl("/login?error=true")
.usernameParameter("uname")
.passwordParameter("pwd");
}
}JWT认证实现要点
- 创建JWT过滤器:
public class JwtAuthenticationFilter extends OncePerRequestFilter {
@Override
protected void doFilterInternal(HttpServletRequest request,
HttpServletResponse response,
FilterChain chain) throws IOException, ServletException {
String token = extractToken(request);
if (token != null && validateToken(token)) {
Authentication auth = createAuthentication(token);
SecurityContextHolder.getContext().setAuthentication(auth);
}
chain.doFilter(request, response);
}
// 其他辅助方法...
}- 配置到安全链中:
@Override
protected void configure(HttpSecurity http) throws Exception {
http.addFilterBefore(jwtAuthenticationFilter(),
UsernamePasswordAuthenticationFilter.class);
}实践建议:
- 生产环境推荐使用
RS256算法而非HS256 - JWT应设置合理的过期时间(建议2-4小时)
- 考虑实现令牌刷新机制
二、授权机制深度剖析
2.1 授权决策流程
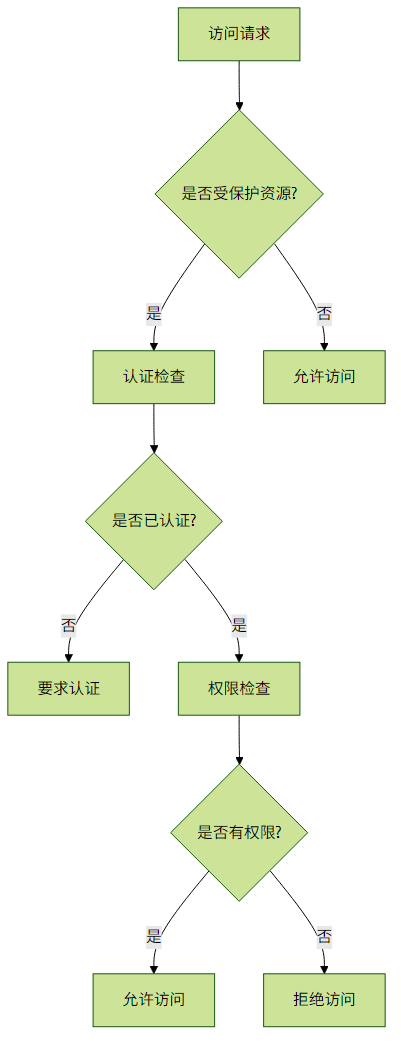
2.2 授权配置方式
URL级别授权
http.authorizeRequests()
.antMatchers("/api/public/**").permitAll()
.antMatchers("/api/admin/**").hasRole("ADMIN")
.antMatchers("/api/user/**").hasAnyRole("USER", "ADMIN")
.antMatchers(HttpMethod.POST, "/api/resources").hasAuthority("WRITE_PRIVILEGE")
.anyRequest().authenticated();方法级别授权
@Service
public class OrderService {
@PreAuthorize("hasRole('USER') and #userId == principal.id")
public List<Order> getUserOrders(Long userId) {
// ...
}
@PostAuthorize("returnObject.owner == principal.username")
public Order getOrderDetails(Long orderId) {
// ...
}
@Secured({"ROLE_ADMIN", "ROLE_SUPERVISOR"})
public void approveOrder(Long orderId) {
// ...
}
}实践建议:
- 优先使用方法级授权,更接近业务逻辑
- 复杂权限逻辑考虑使用
@PostAuthorize - 对于REST API,推荐结合
@ResponseStatus返回明确状态码
2.3 动态权限实现
自定义权限投票器示例:
public class TimeBasedVoter implements AccessDecisionVoter<Object> {
@Override
public boolean supports(ConfigAttribute attribute) {
return attribute.getAttribute().startsWith("TIME_");
}
@Override
public int vote(Authentication authentication, Object object,
Collection<ConfigAttribute> attributes) {
// 实现基于时间的访问控制逻辑
}
}注册自定义投票器:
@Bean
public AccessDecisionManager accessDecisionManager() {
List<AccessDecisionVoter<?>> voters = Arrays.asList(
new RoleVoter(),
new TimeBasedVoter(),
new AuthenticatedVoter()
);
return new UnanimousBased(voters);
}三、安全防护最佳实践
3.1 CSRF防护机制
工作原理:
- 服务器生成CSRF令牌
- 令牌存储在会话和表单隐藏字段中
- 提交请求时验证令牌一致性
定制配置:
http.csrf()
.csrfTokenRepository(CookieCsrfTokenRepository.withHttpOnlyFalse())
.ignoringAntMatchers("/api/external/**");3.2 CORS配置
@Bean
public CorsConfigurationSource corsConfigurationSource() {
CorsConfiguration config = new CorsConfiguration();
config.setAllowedOrigins(Arrays.asList("https://trusted.com"));
config.setAllowedMethods(Arrays.asList("GET", "POST"));
config.setAllowCredentials(true);
UrlBasedCorsConfigurationSource source = new UrlBasedCorsConfigurationSource();
source.registerCorsConfiguration("/api/**", config);
return source;
}3.3 会话管理
http.sessionManagement()
.sessionFixation().migrateSession()
.maximumSessions(1)
.maxSessionsPreventsLogin(true)
.expiredUrl("/login?expired");安全建议表:
| 攻击类型 | 防护措施 | 配置示例 |
|---|---|---|
| CSRF | 启用CSRF防护 | .csrf().csrfTokenRepository(...) |
| 点击劫持 | X-Frame-Options | headers().frameOptions().sameOrigin() |
| XSS | 内容安全策略 | headers().contentSecurityPolicy("default-src 'self'") |
| 会话固定 | 会话迁移 | sessionManagement().sessionFixation().migrateSession() |
四、过滤器链定制策略
4.1 核心过滤器顺序
Spring Security过滤器链的典型顺序:
ChannelProcessingFilterWebAsyncManagerIntegrationFilterSecurityContextPersistenceFilterHeaderWriterFilterCorsFilterCsrfFilterLogoutFilterUsernamePasswordAuthenticationFilterDefaultLoginPageGeneratingFilterBasicAuthenticationFilterRequestCacheAwareFilterSecurityContextHolderAwareRequestFilterAnonymousAuthenticationFilterSessionManagementFilterExceptionTranslationFilterFilterSecurityInterceptor
4.2 自定义过滤器插入
public class CustomAuthFilter extends GenericFilterBean {
@Override
public void doFilter(ServletRequest request, ServletResponse response,
FilterChain chain) throws IOException, ServletException {
// 前置处理逻辑
chain.doFilter(request, response);
// 后置处理逻辑
}
}
// 配置类中注册
http.addFilterBefore(new CustomAuthFilter(), UsernamePasswordAuthenticationFilter.class);
// 或
http.addFilterAfter(new CustomAuthFilter(), BasicAuthenticationFilter.class);最佳实践:
- 明确过滤器的执行位置需求
- 避免在过滤器中执行耗时操作
- 考虑过滤器之间的依赖关系
五、OAuth2与JWT深度集成
5.1 资源服务器配置
@EnableResourceServer
@Configuration
public class ResourceServerConfig extends ResourceServerConfigurerAdapter {
@Override
public void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/api/public/**").permitAll()
.antMatchers("/api/**").authenticated();
}
@Override
public void configure(ResourceServerSecurityConfigurer resources) {
resources.tokenServices(tokenServices());
}
@Bean
public TokenStore tokenStore() {
return new JwtTokenStore(jwtAccessTokenConverter());
}
@Bean
public JwtAccessTokenConverter jwtAccessTokenConverter() {
JwtAccessTokenConverter converter = new JwtAccessTokenConverter();
converter.setSigningKey("secret-key");
return converter;
}
}5.2 JWT令牌增强
自定义令牌增强器:
public class CustomTokenEnhancer implements TokenEnhancer {
@Override
public OAuth2AccessToken enhance(OAuth2AccessToken accessToken,
OAuth2Authentication authentication) {
Map<String, Object> additionalInfo = new HashMap<>();
// 添加自定义声明
additionalInfo.put("organization", authentication.getName() + "_ORG");
((DefaultOAuth2AccessToken) accessToken).setAdditionalInformation(additionalInfo);
return accessToken;
}
}JWT最佳实践:
- 使用强密码算法(推荐RS256)
- 设置合理的过期时间(访问令牌1-2小时,刷新令牌7-30天)
- 不要在JWT中存储敏感信息
- 实现令牌吊销机制
六、性能优化与疑难解答
6.1 性能优化技巧
缓存用户数据:
@Bean public UserDetailsService userDetailsService() { return new CachingUserDetailsService(new JdbcDaoImpl()); }优化密码编码器:
@Bean public PasswordEncoder passwordEncoder() { // 根据安全需求选择合适的编码器 return new BCryptPasswordEncoder(12); // 调整强度参数 }减少不必要的过滤器:
http.securityContext().disable() .sessionManagement().disable(); // 仅适用于无状态API
6.2 常见问题解决
问题1:认证成功但权限不生效
- 检查
@EnableGlobalMethodSecurity是否启用 - 确认角色前缀配置(默认添加
ROLE_) - 检查权限缓存是否及时更新
问题2:循环依赖
@Bean
public PasswordEncoder passwordEncoder() {
return PasswordEncoderFactories.createDelegatingPasswordEncoder();
}
@Bean
@DependsOn("passwordEncoder") // 显式声明依赖
public UserDetailsService userDetailsService() {
// ...
}问题3:静态资源被拦截
@Override
public void configure(WebSecurity web) {
web.ignoring().antMatchers("/css/**", "/js/**", "/images/**");
}通过以上深度解析,开发者可以全面掌握Spring Security的核心机制,并能在实际项目中灵活应用各种安全策略。
评论已关闭