Spring Security响应式安全与微服务实践指南
Spring Security高级主题:响应式安全与微服务深度实践
1. 响应式安全(Spring WebFlux)
核心概念
在响应式编程模型中,Spring Security通过SecurityWebFilterChain替代传统的FilterChain,完全基于Reactor实现非阻塞安全控制。
@EnableWebFluxSecurity
public class ReactiveSecurityConfig {
@Bean
public SecurityWebFilterChain securityWebFilterChain(ServerHttpSecurity http) {
return http
.authorizeExchange()
.pathMatchers("/admin/**").hasAuthority("ROLE_ADMIN")
.anyExchange().authenticated()
.and()
.httpBasic()
.and()
.formLogin()
.and().build();
}
}关键差异点:
- 使用
ServerHttpSecurity而非HttpSecurity authorizeExchange()替代authorizeRequests()pathMatchers()替代antMatchers()
响应式用户服务
@Bean
public ReactiveUserDetailsService userDetailsService() {
return username ->
reactiveUserRepository.findByUsername(username)
.map(user -> User.withUsername(user.getUsername())
.password(user.getPassword())
.authorities(user.getRoles())
.build());
}实践建议:
- 所有安全操作必须返回
Mono或Flux - 避免在响应式链中执行阻塞操作
- 使用
ServerSecurityContextRepository自定义上下文存储
2. 微服务安全架构
Spring Cloud Gateway集成
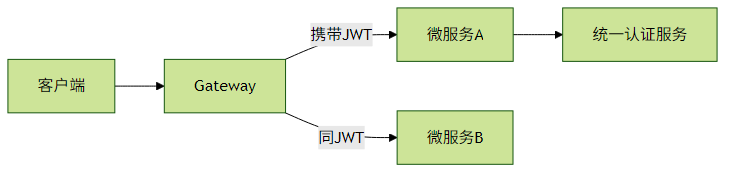
网关配置示例:
spring:
cloud:
gateway:
routes:
- id: auth-service
uri: lb://auth-service
predicates:
- Path=/auth/**
filters:
- StripPrefix=1
- id: resource-service
uri: lb://resource-service
predicates:
- Path=/api/**
filters:
- JwtRelay=OAuth2多租户配置
@Bean
public JwtDecoder jwtDecoder(TenantResolver tenantResolver) {
return token -> {
String issuer = getIssuer(token);
Tenant tenant = tenantResolver.resolve(issuer);
return NimbusJwtDecoder.withJwkSetUri(tenant.getJwkSetUrl())
.build()
.decode(token);
};
}多租户实现要点:
- 自定义
TenantResolver解析租户信息 - 每个租户独立的JWK Set URL
- 缓存解码器避免重复创建
3. 自定义扩展实践
认证异常处理
@Component
public class JwtAuthenticationEntryPoint implements AuthenticationEntryPoint {
@Override
public void commence(HttpServletRequest request,
HttpServletResponse response,
AuthenticationException authException) {
response.setContentType("application/json");
response.setStatus(HttpStatus.UNAUTHORIZED.value());
response.getWriter().write(
new ObjectMapper().writeValueAsString(
Map.of("error", "TOKEN_INVALID",
"message", authException.getMessage())
));
}
}动态权限控制
public class DynamicPermissionEvaluator implements PermissionEvaluator {
@Override
public boolean hasPermission(Authentication auth,
Object target,
Object permission) {
String targetType = target.getClass().getSimpleName();
return permissionCheckService.checkAccess(
auth.getName(),
targetType,
permission.toString());
}
}注册自定义评估器:
@Configuration
@EnableGlobalMethodSecurity(prePostEnabled = true)
public class MethodSecurityConfig extends GlobalMethodSecurityConfiguration {
@Override
protected MethodSecurityExpressionHandler createExpressionHandler() {
DefaultMethodSecurityExpressionHandler handler =
new DefaultMethodSecurityExpressionHandler();
handler.setPermissionEvaluator(new DynamicPermissionEvaluator());
return handler;
}
}4. 安全测试策略
控制器测试
@Test
@WithMockUser(roles = "ADMIN")
public void testAdminEndpoint() throws Exception {
mockMvc.perform(get("/admin/users"))
.andExpect(status().isOk());
}
@Test
public void testUnauthenticated() throws Exception {
mockMvc.perform(get("/api/data"))
.andExpect(status().isUnauthorized());
}过滤器测试
@Test
public void testJwtFilter() {
MockHttpServletRequest request = new MockHttpServletRequest();
request.addHeader("Authorization", "Bearer invalid_token");
JwtAuthenticationFilter filter = new JwtAuthenticationFilter();
FilterChainProxy filterChain = new FilterChainProxy(
new DefaultSecurityFilterChain(new AntPathRequestMatcher("/**")));
MockHttpServletResponse response = new MockHttpServletResponse();
filter.doFilter(request, response, (req, res) -> {});
assertEquals(401, response.getStatus());
}测试最佳实践:
- 使用
@WithSecurityContext创建复杂测试场景 - 对
SecurityContext进行独立测试 - 验证过滤器的执行顺序
- 模拟CSRF令牌测试防护机制
深度优化建议
响应式性能调优:
- 使用
WebSessionServerSecurityContextRepository替代默认存储 - 配置合理的
SecurityContext订阅超时
- 使用
微服务安全增强:
@Bean public ServerAuthenticationConverter authenticationConverter() { return exchange -> { String token = extractToken(exchange.getRequest()); return Mono.just(new BearerTokenAuthenticationToken(token)); }; }租户隔离策略:
public class TenantAwareJwtDecoder implements JwtDecoder { private final Map<String, JwtDecoder> tenantDecoders; @Override public Jwt decode(String token) { String tenant = resolveTenant(token); return tenantDecoders.get(tenant).decode(token); } }
通过以上高级实践,可构建适应云原生架构的企业级安全方案,兼顾灵活性与高性能。
评论已关闭