Spring Security认证授权机制深度解析
Spring Security 认证与授权机制深度解析
一、认证机制详解
1.1 认证流程核心组件
Spring Security 的认证流程围绕 AuthenticationManager 展开,其标准实现 ProviderManager 通过委托给多个 AuthenticationProvider 来完成实际认证工作。
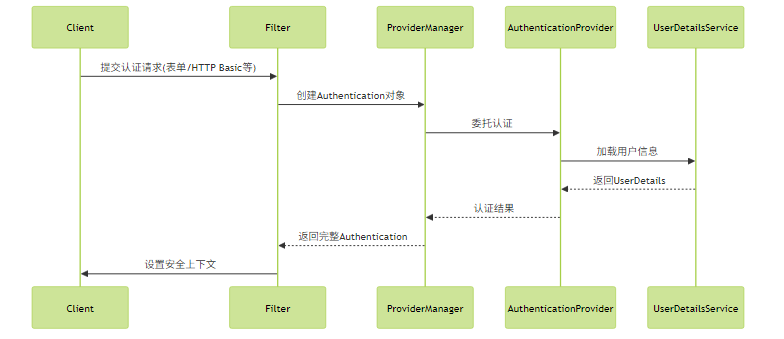
1.2 自定义认证扩展
实践建议:当需要集成企业LDAP或自定义认证源时,优先实现 AuthenticationProvider 而非直接修改 UserDetailsService
public class CustomAuthenticationProvider implements AuthenticationProvider {
@Override
public Authentication authenticate(Authentication auth) {
String username = auth.getName();
String password = auth.getCredentials().toString();
// 调用企业认证服务
User user = enterpriseAuthService.authenticate(username, password);
if (user == null) {
throw new BadCredentialsException("认证失败");
}
return new UsernamePasswordAuthenticationToken(
user,
password,
AuthorityUtils.createAuthorityList("ROLE_USER")
);
}
@Override
public boolean supports(Class<?> authentication) {
return authentication.equals(UsernamePasswordAuthenticationToken.class);
}
}二、授权机制深度剖析
2.1 授权决策三阶段
- 配置阶段:通过
HttpSecurity或注解定义权限规则 - 决策阶段:
AccessDecisionManager协调多个AccessDecisionVoter - 执行阶段:
FilterSecurityInterceptor实施最终决策
// 动态权限配置示例
@Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
.antMatchers("/projects/**")
.access("@permissionService.hasProjectAccess(authentication,#projectId)")
.anyRequest().authenticated();
}2.2 方法级权限控制对比
| 注解 | 特点 | 适用场景 |
|---|---|---|
@Secured | 仅支持角色检查,简单直接 | 简单角色控制 |
@PreAuthorize | 支持SpEL表达式,功能最强大 | 复杂业务逻辑权限判断 |
@PostAuthorize | 方法执行后检查返回值 | 敏感数据返回过滤 |
实践建议:生产环境推荐使用 @PreAuthorize 配合自定义PermissionEvaluator
@PreAuthorize("hasPermission(#projectId, 'project', 'read')")
public Project getProject(String projectId) {
return projectRepository.findById(projectId);
}三、安全防护最佳实践
3.1 CSRF防护机制
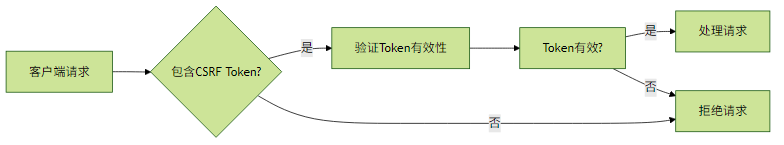
关键配置:
@Override
protected void configure(HttpSecurity http) throws Exception {
http.csrf()
.csrfTokenRepository(CookieCsrfTokenRepository.withHttpOnlyFalse())
.ignoringAntMatchers("/api/external/**");
}3.2 会话安全配置
# application.properties
server.servlet.session.timeout=30m
spring.session.redis.flush-mode=on_save
spring.session.redis.namespace=spring:session防护策略:
- 启用会话固定保护:
http.sessionManagement().sessionFixation().migrateSession() - 并发会话控制:
http.sessionManagement().maximumSessions(1)
四、OAuth2与JWT集成
4.1 资源服务器配置
@EnableResourceServer
@Configuration
public class ResourceServerConfig extends ResourceServerConfigurerAdapter {
@Override
public void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/api/public/**").permitAll()
.antMatchers("/api/**").authenticated();
}
@Override
public void configure(ResourceServerSecurityConfigurer resources) {
resources.tokenServices(jwtTokenServices());
}
@Bean
public JwtAccessTokenConverter jwtAccessTokenConverter() {
JwtAccessTokenConverter converter = new JwtAccessTokenConverter();
converter.setSigningKey("secret-key");
return converter;
}
}4.2 JWT过滤器实现
public class JwtAuthenticationFilter extends OncePerRequestFilter {
@Override
protected void doFilterInternal(HttpServletRequest request,
HttpServletResponse response,
FilterChain chain) {
String token = extractToken(request);
if (token != null && validateToken(token)) {
Authentication auth = createAuthentication(token);
SecurityContextHolder.getContext().setAuthentication(auth);
}
chain.doFilter(request, response);
}
private Authentication createAuthentication(String token) {
Claims claims = Jwts.parser().parseClaimsJws(token).getBody();
return new JwtAuthenticationToken(claims.getSubject(),
AuthorityUtils.commaSeparatedStringToAuthorityList(
claims.get("roles", String.class)));
}
}五、性能优化建议
缓存用户权限:实现带缓存的
UserDetailsService@Service public class CachingUserDetailsService implements UserDetailsService { @Cacheable(value = "userDetails", key = "#username") public UserDetails loadUserByUsername(String username) { // 原始查询逻辑 } }无状态架构:结合JWT禁用会话
http.sessionManagement() .sessionCreationPolicy(SessionCreationPolicy.STATELESS);密码编码优化:使用Argon2替代BCrypt
@Bean public PasswordEncoder passwordEncoder() { return new Argon2PasswordEncoder(); }
通过以上深度解析,开发者可以全面掌握Spring Security的核心机制,并能在实际项目中灵活应用各种安全策略。
评论已关闭