Spring Security认证扩展:MFA与生物识别集成指南
Spring Security认证机制扩展实战
一、多因素认证(MFA)集成
1. TOTP验证码集成
TOTP(基于时间的一次性密码)是MFA的常用方案,Spring Security可通过自定义AuthenticationProvider实现:
public class TotpAuthenticationProvider implements AuthenticationProvider {
private final UserDetailsService userDetailsService;
private final TotpService totpService;
@Override
public Authentication authenticate(Authentication auth) {
String username = auth.getName();
String code = (String) auth.getCredentials();
UserDetails user = userDetailsService.loadUserByUsername(username);
if (totpService.verifyCode(user.getTotpSecret(), code)) {
return new UsernamePasswordAuthenticationToken(
user, null, user.getAuthorities());
}
throw new BadCredentialsException("Invalid TOTP code");
}
}实践建议:
- 使用Google Authenticator或Authy等标准TOTP算法库
- 密钥存储应加密,推荐使用HSM或KMS服务
- 提供备用验证方式(如短信/邮件)应对设备丢失情况
2. 二次验证拦截流程
自定义过滤器实现二次验证拦截:
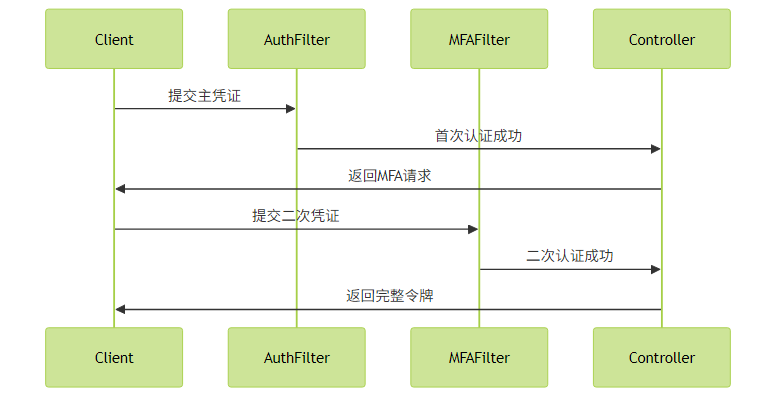
实现代码示例:
public class MfaFilter extends OncePerRequestFilter {
@Override
protected void doFilterInternal(HttpServletRequest request,
HttpServletResponse response,
FilterChain chain) {
if (requiresMfa(request) {
if (!isMfaVerified(request)) {
response.sendError(401, "MFA required");
return;
}
}
chain.doFilter(request, response);
}
}二、生物识别认证集成
1. 指纹认证适配
通过AuthenticationDetailsSource集成生物特征:
public class BiometricAuthenticationDetails
implements AuthenticationDetailsSource<HttpServletRequest, WebAuthenticationDetails> {
@Override
public WebAuthenticationDetails buildDetails(HttpServletRequest context) {
String fingerprintData = context.getHeader("X-Fingerprint-Token");
return new BiometricDetails(fingerprintData);
}
}
// 配置
http.formLogin()
.authenticationDetailsSource(new BiometricAuthenticationDetails());关键考虑:
- 生物特征应作为辅助因素而非唯一凭证
- 原始生物数据不应存储,应保存加密后的特征模板
- 符合GDPR等隐私法规要求
2. 面部识别流程
@RestController
public class FaceAuthController {
@PostMapping("/auth/face")
public ResponseEntity<?> authenticateFace(@RequestBody FaceAuthRequest request) {
FaceVerificationResult result = faceService.verify(
request.getVideoHash(),
request.getLivenessData());
if (result.isVerified()) {
Authentication auth = new FaceAuthenticationToken(result.getUserId());
SecurityContextHolder.getContext().setAuthentication(auth);
return ResponseEntity.ok().build();
}
return ResponseEntity.status(401).build();
}
}三、OAuth2深度扩展
1. 动态客户端注册(RFC 7591)
实现ClientRegistrationRepository:
public class DynamicClientRegistrationRepository
implements ClientRegistrationRepository {
private final ClientRegistrationService registrationService;
@Override
public ClientRegistration findByRegistrationId(String id) {
return registrationService.findByRegistrationId(id)
.orElseThrow(() -> new IllegalArgumentException("Invalid client"));
}
}
// 注册端点
@PostMapping("/connect/register")
public ClientRegistration registerClient(
@Valid @RequestBody RegistrationRequest request) {
return registrationService.register(request);
}最佳实践:
- 必须实现客户端元数据验证
- 支持软件声明(Software Statements)
- 记录完整的审计日志
2. JWT自省端点定制
扩展OAuth2TokenIntrospectionEndpointConfigurer:
@Override
public void configure(AuthorizationServerEndpointsConfigurer endpoints) {
endpoints.tokenIntrospectionEndpoint()
.introspectionResponseHandler(customResponseHandler())
.introspectionRequestConverter(customRequestConverter());
}
private OAuth2TokenIntrospectionResponseHandler customResponseHandler() {
return (claims, authentication) -> {
Map<String, Object> response = new HashMap<>();
response.put("active", true);
response.put("custom_field", "special_value");
return response;
};
}关键问题解决方案
MFA状态保持问题
- 使用
AuthenticationTrustResolver区分认证阶段 - 临时状态可存储在分布式缓存中
- 使用
生物特征认证降级方案
if (biometricAuthFailed && fallbackEnabled) { triggerSmsFallback(user); }动态客户端密钥轮换
public void rotateClientSecret(String clientId) { Client client = clientRepository.findById(clientId); client.setSecret(encoder.encode(generateNewSecret())); client.setPreviousSecret(currentSecret); clientRepository.save(client); }
性能优化建议
- TOTP验证应使用高效哈希算法(如SHA-256)
- 生物特征比对采用异步处理
- JWT自省结果应缓存,设置合理的TTL
通过以上扩展机制,Spring Security可以满足现代应用复杂的安全认证需求,建议根据实际业务场景选择合适的组合方案。
评论已关闭