Spring Security响应式实践:WebFlux与RSocket安全配置
响应式安全:Spring Security在WebFlux与RSocket中的实践
一、WebFlux安全配置
在响应式编程范式中,Spring Security提供了专门针对WebFlux的安全支持,其核心配置方式与传统Servlet环境有显著差异。
1. ServerSecurityContextRepository实现
ServerSecurityContextRepository是响应式环境中存储安全上下文的核心接口,替代了Servlet中的SecurityContextRepository。
public interface ServerSecurityContextRepository {
Mono<Void> save(ServerWebExchange exchange, SecurityContext context);
Mono<SecurityContext> load(ServerWebExchange exchange);
}典型实现示例(基于JWT的存储):
public class JwtServerSecurityContextRepository implements ServerSecurityContextRepository {
private final ReactiveJwtDecoder jwtDecoder;
@Override
public Mono<SecurityContext> load(ServerWebExchange exchange) {
return Mono.justOrEmpty(exchange.getRequest().getHeaders().getFirst("Authorization"))
.filter(authHeader -> authHeader.startsWith("Bearer "))
.map(authHeader -> authHeader.substring(7))
.flatMap(token -> jwtDecoder.decode(token))
.map(jwt -> {
List<GrantedAuthority> authorities = jwt.getClaimAsStringList("scope")
.stream()
.map(SimpleGrantedAuthority::new)
.collect(Collectors.toList());
return new UsernamePasswordAuthenticationToken(
jwt.getSubject(), null, authorities);
})
.map(authentication -> new SecurityContextImpl(authentication));
}
@Override
public Mono<Void> save(ServerWebExchange exchange, SecurityContext context) {
return Mono.empty(); // 无状态场景无需保存
}
}实践建议:
- 无状态服务建议返回
Mono.empty()的save实现 - 分布式场景可结合Redis实现响应式上下文存储
- 注意线程安全,避免在操作链中阻塞
2. 响应式认证管理器(ReactiveAuthenticationManager)
响应式认证管理器处理实际的认证逻辑,其核心特点是返回Mono<Authentication>。
@Bean
public ReactiveAuthenticationManager authenticationManager(
ReactiveUserDetailsService userDetailsService,
PasswordEncoder passwordEncoder) {
var authenticationManager = new UserDetailsRepositoryReactiveAuthenticationManager(
userDetailsService);
authenticationManager.setPasswordEncoder(passwordEncoder);
return authenticationManager;
}自定义认证流程示例:
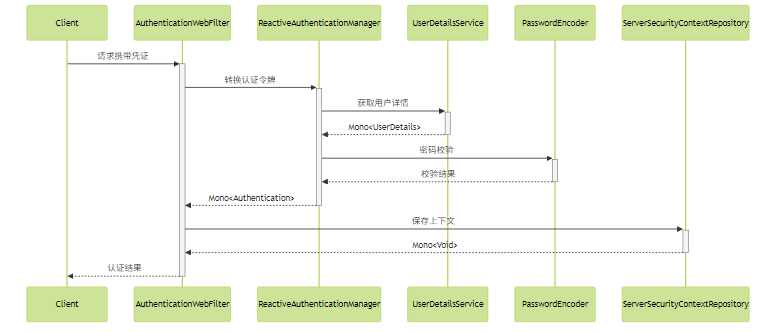
关键配置示例:
@Bean
public SecurityWebFilterChain securityWebFilterChain(ServerHttpSecurity http) {
return http
.authorizeExchange()
.pathMatchers("/public/**").permitAll()
.anyExchange().authenticated()
.and()
.httpBasic().disable()
.formLogin().disable()
.csrf().disable()
.authenticationManager(authenticationManager)
.securityContextRepository(securityContextRepository)
.addFilterAt(new JwtAuthenticationWebFilter(authenticationManager), SecurityWebFiltersOrder.AUTHENTICATION)
.build();
}二、RSocket安全
RSocket作为响应式应用间通信协议,其安全机制与传统HTTP有显著不同。
基于JWT的RSocket认证
服务端配置:
@Bean
public RSocketSecurity rSocketSecurity() {
return RSocketSecurityConfigurer
.jwt(jwt -> jwt
.authenticationManager(jwtReactiveAuthenticationManager)
.publicKey(publicKey)
)
.authorizePayload(authorize -> authorize
.anyRequest().authenticated()
.anyExchange().permitAll()
)
.simpleAuthentication(Customizer.withDefaults());
}客户端认证流程:
@Bean
public RSocketRequester rSocketRequester(RSocketRequester.Builder builder) {
String token = generateJwtToken(); // 生成或获取JWT
return builder
.setupMetadata(token, MimeTypeUtils.parseMimeType("message/x.rsocket.authentication.v0"))
.connectTcp("localhost", 7000)
.block();
}安全元数据类型:
| 类型 | MIME Type | 描述 |
|---|---|---|
| Basic Auth | message/x.rsocket.authentication.basic.v0 | 基本认证 |
| JWT | message/x.rsocket.authentication.v0 | JWT令牌 |
| 自定义 | 自定义类型 | 需双方约定 |
路由级权限控制:
@MessageMapping("secure.transaction")
@PreAuthorize("hasRole('FINANCE')")
public Mono<TransactionResult> processTransaction(TransactionRequest request) {
// 业务逻辑
}实践建议:
- 使用TLS加密RSocket通信链路
- 短期有效的JWT令牌(建议<5分钟)
- 实现令牌刷新机制
- 监控异常认证尝试
三、性能优化策略
响应式缓存:
@Bean public ReactiveAuthenticationManager cachedAuthManager( ReactiveAuthenticationManager delegate) { return new CachingReactiveAuthenticationManager(delegate); }背压处理:
public class BackpressureAwareAuthManager implements ReactiveAuthenticationManager { @Override public Mono<Authentication> authenticate(Authentication authentication) { return Mono.just(authentication) .publishOn(Schedulers.boundedElastic()) // 防止主线程阻塞 .timeout(Duration.ofSeconds(3)) // 超时控制 .onErrorResume(e -> Mono.empty()); // 优雅降级 } }监控指标:
@Bean public MeterRegistryCustomizer<MeterRegistry> securityMetrics() { return registry -> { Metrics.timer("security.authentication.attempts") .description("Authentication latency") .register(registry); }; }
常见问题解决方案
问题1:WebFlux中CSRF防护失效
- 原因:响应式环境需要显式配置
解决:
http.csrf(csrf -> csrf.csrfTokenRepository(CookieServerCsrfTokenRepository.withHttpOnlyFalse()))
问题2:RSocket连接认证失败
- 检查:确保元数据正确设置且服务端支持相同认证协议
调试:启用RSocket帧日志
logging.level.io.rsocket=frames
问题3:响应式上下文传递中断
- 方案:使用
Hooks.onOperatorDebug()定位上下文丢失点 替代:显式传递上下文参数
public Mono<String> getData(ServerWebExchange exchange) { return exchange.getPrincipal() .flatMap(principal -> reactiveService.getData(principal.getName())); }
通过以上实践,可以构建既安全又高效的响应式应用系统。
评论已关闭